In a world of many networks that can be encountered with a variety of technical hacking, one of which ARP Spoofing or ARP Poisoning. In this blog I will explain what it is ARP spoofing. nah, just, Address Resolution Protocol (ARP) spoofing or ARP Pollution Routing Gateway in a LAN & WIFI network, by using ARP Spoofing techniques this hackers / crackers can be a gateway while making it able to analyze network traffic data LAN & WIFI victims, with this technique uses the hacker was able to obtain email passwords, credit cards and many others, with this technique also hacker / crackers capable of deciding your LAN network with the workings of Denial of service attack that can break the network LAN & Wifi Victims.
An application tools to analyze the packets of the protocol we use a tool called WireShark on http://www.wireshark.org download at the site. We will do ARP spoofing by using the script "arpret.c" scripts are created with the C programming language that works by sending fake ARP reply to the host and target can only run in the Linux operating system. Slackware Linux 12.1 version running on a computer bug that is running the script has the IP address 192.168.10.22 with MAC 00:1 e: ec: c4: 86:67 otherwise it could be setting the kernel to forward packets to other destinations in other words, forwarding packets which has been received.
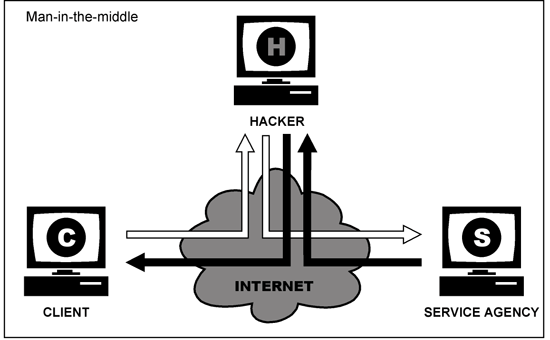
One example of ARP spoofing is to attack man-in-the-middle, where the attacker (PC 3) deceiving a computer to trust the attacker is a computer 2, and vice versa, have access to all the posts from both sides of direction without any barriers kriptanalisis effort.
The attacker must monitor the packets sent from one computer to computer 2, and then analyze the number of these packages. Then the attacker to attack a computer with SYN attack and injects his own packets, claiming to have a computer address. A computer firewall against several attacks swindle if he had ditatarajahkan with knowledge of all the IP addresses which are connected with each of her face. then mendekteksi package swindle when he arrived at between the unknown face continued on an IP address.
Many protocols are not designed with careful ruse is exposed to the attacks, including those widely used in Internet.
Swindle caller ID
In the public telephone network, it has long be known who is calling by looking at the caller ID information is transmitted once the call. There is a technology which transmits this information to the phone line, mobile and VoIP. Unfortunately, there are now technologies (especially associated with VoIP) that allows the caller to deceive their identity, and giving a false name and phone number, which can be used as a tool to cheat or disrupt. Therefore there are services and gateways that menyalinghubungkan VoIP public telephone network with others, fake caller ID can be transmitted to the phone anywhere on the planet, then nearly lost its usefulness cause the caller ID. Because of the geographical nature of teragih Internet, VoIP calls can be made in different countries with the receiver, meaning it is difficult to make laws to control those who use fake caller ID to conspire.
Tags:
Internet Security